-
Capacitación
VPN Encapsulation Technology
Tiempo de liberación:Aug 01, 2017
1. Overview
GRE (Generic Routing Encapsulation) is a protocol that encapsulates data packets of certain network layer protocols (such as IP and IPX) so that these encapsulated data packets can be transmitted over another network layer protocol (such as IP). In most normal cases, a system has a payload (or load) packet that needs to be encapsulated and delivered to a destination network. The payload is first encapsulated in a GRE packet, and then the GRE packet is encapsulated in another protocol and forwarded. This protocol is forwarding protocol. Using Tunnel (tunnel) technology, GRE is a VPN (Virtual Private Network) layer 3 tunneling protocol. Tunnel is a virtual point-to-point connection that provides a path for transmission of encapsulated data packets, and the data packets are encapsulated and decapsulated at both endpoints of the Tunnel.
2. Why is GRE used for tunneling?
GRE is a tunneling protocol originally developed by CISCO. It provides a simple generic approach to transport packets of one protocol over another protocol by means of encapsulation, so that packets can be transmitted in heterogeneous networks. For example, if we need to carry out non-IP transmission over IP network, then the GRE protocol is good solution for data transmission; for another example, you can transmit multicast packets and IPv6 packets through GRE tunnel. Sometimes you need encrypted multicast transmission, and GRE tunnels can deliver multicast packets like a physical network interface. In addition, a large number of videos, VoIPs, and music streams are applicable to multicast transmission. At present, computers inside enterprises communicate using private IP address. When an enterprise needs to connect with its branch in other area via Internet, it is necessary to solve the problem of traversing private network IP through public network. A very simple solution is: create a “tunnel” in the Internet, through which the enterprise and its branch can realize interconnection. GRE technology can effectively solve this problem.·
3. GRE Advantages
Both PPTP and L2TP provide incomplete support for modern security needs, and their scope of application is not wide enough. Taking PPTP as an example, it does not support QOS, and its authentication and encryption are relatively fragile. In addition, each user can only use a tunnel, so from the perspective of user, a large amount of resources will be wasted while a great deal of money will be spent. In fact, they all lack the digital certificate supported by PKI technology, so VPN is short of the most important security. GRE is a layer 3 tunneling protocol. It is easy to configure and operate, and its security, scalability and reliability are stronger than the layer 2 tunneling protocol. And our GRE can be used with IPSec which provides encryption for user data, so that security for user is higher. The protocol provides encryption and authentication for communication between routers, firewalls, or during other communications. It is much more secure than any other protocols. Since GRE is a protocol over IP networks, it is very easy to form a specification around the world, thus featuring an excellent versatility. In the relatively secure Intranet of a company or enterprise, if the GRE protocol can be flexibly applied in an independent manner, it can meet a variety of business needs and receive a great effect, even better than other technologies.
4. GRE Characteristics
(1)GRE is easy to implement and increases only a few loads on devices at both ends of a tunnel.
(2)GRE is easy to encapsulate data packets of non-IP protocol, such as IPX or AppleTalk data packets.
(3)Data communication is limited to be carried out in single private IP network.
(4)GRE supports multiple protocols and multicast transmission.
(5)GRE can be used to create flexible VPN.
(6) GRE supports multipoint tunnel. ·
(7) GRE is able to implement QOS.
4. Device Basic Configuration
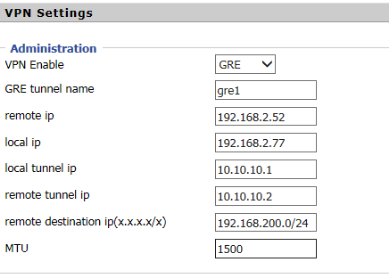
Device 1 settings are as follows:
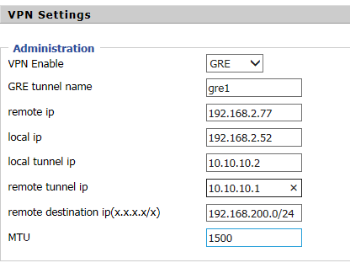
Device 2 settings are as follows:
5. Conclusion
Proposed earlier, GRE provides a strong ability to encapsulate data packets. Up to today, it has been developed to be relatively mature. It is not limited to a particular "X over B" application, but a common encapsulating method. GRE can be used with IPSec, to provide users with a more secure and reliable environment. In the actual networking, GRE supports more flexible use.
GRE (Generic Routing Encapsulation) is a protocol that encapsulates data packets of certain network layer protocols (such as IP and IPX) so that these encapsulated data packets can be transmitted over another network layer protocol (such as IP). In most normal cases, a system has a payload (or load) packet that needs to be encapsulated and delivered to a destination network. The payload is first encapsulated in a GRE packet, and then the GRE packet is encapsulated in another protocol and forwarded. This protocol is forwarding protocol. Using Tunnel (tunnel) technology, GRE is a VPN (Virtual Private Network) layer 3 tunneling protocol. Tunnel is a virtual point-to-point connection that provides a path for transmission of encapsulated data packets, and the data packets are encapsulated and decapsulated at both endpoints of the Tunnel.
2. Why is GRE used for tunneling?
GRE is a tunneling protocol originally developed by CISCO. It provides a simple generic approach to transport packets of one protocol over another protocol by means of encapsulation, so that packets can be transmitted in heterogeneous networks. For example, if we need to carry out non-IP transmission over IP network, then the GRE protocol is good solution for data transmission; for another example, you can transmit multicast packets and IPv6 packets through GRE tunnel. Sometimes you need encrypted multicast transmission, and GRE tunnels can deliver multicast packets like a physical network interface. In addition, a large number of videos, VoIPs, and music streams are applicable to multicast transmission. At present, computers inside enterprises communicate using private IP address. When an enterprise needs to connect with its branch in other area via Internet, it is necessary to solve the problem of traversing private network IP through public network. A very simple solution is: create a “tunnel” in the Internet, through which the enterprise and its branch can realize interconnection. GRE technology can effectively solve this problem.·
3. GRE Advantages
Both PPTP and L2TP provide incomplete support for modern security needs, and their scope of application is not wide enough. Taking PPTP as an example, it does not support QOS, and its authentication and encryption are relatively fragile. In addition, each user can only use a tunnel, so from the perspective of user, a large amount of resources will be wasted while a great deal of money will be spent. In fact, they all lack the digital certificate supported by PKI technology, so VPN is short of the most important security. GRE is a layer 3 tunneling protocol. It is easy to configure and operate, and its security, scalability and reliability are stronger than the layer 2 tunneling protocol. And our GRE can be used with IPSec which provides encryption for user data, so that security for user is higher. The protocol provides encryption and authentication for communication between routers, firewalls, or during other communications. It is much more secure than any other protocols. Since GRE is a protocol over IP networks, it is very easy to form a specification around the world, thus featuring an excellent versatility. In the relatively secure Intranet of a company or enterprise, if the GRE protocol can be flexibly applied in an independent manner, it can meet a variety of business needs and receive a great effect, even better than other technologies.
4. GRE Characteristics
(1)GRE is easy to implement and increases only a few loads on devices at both ends of a tunnel.
(2)GRE is easy to encapsulate data packets of non-IP protocol, such as IPX or AppleTalk data packets.
(3)Data communication is limited to be carried out in single private IP network.
(4)GRE supports multiple protocols and multicast transmission.
(5)GRE can be used to create flexible VPN.
(6) GRE supports multipoint tunnel. ·
(7) GRE is able to implement QOS.
4. Device Basic Configuration
Device 1 settings are as follows:

Device 2 settings are as follows:

5. Conclusion
Proposed earlier, GRE provides a strong ability to encapsulate data packets. Up to today, it has been developed to be relatively mature. It is not limited to a particular "X over B" application, but a common encapsulating method. GRE can be used with IPSec, to provide users with a more secure and reliable environment. In the actual networking, GRE supports more flexible use.










 volver a la lista
volver a la lista