-
Capacitación
802.1x Overview
Tiempo de liberación:Jul 03, 2018
1.Background
About the Ethernet defined by the IEEE 802 previously, if there is a physical connection port, unauthorized network devices or users can connect to the Ethernet through the physical port then they can do anything use the network. With the wide application of local area network technology, especially in the application of the operation network, the use of the local area network, which does not distinguish between the users, is increasingly detrimental to the network environment. How to make use of the simple and inexpensive networking features of LAN technology and at the same time provide authentication for the legitimacy of users or devices accessing the network is the focus of discussion in the industry.
2. What is 802.1x
The 802.1X protocol is a port-based network access control protocol. "Port-based network access control" refers to the authentication and control of the accessed user equipment at the port level of the LAN access device. When you use a new device to access the network, you need to use an authorized user name and password to perform various Internet operations.
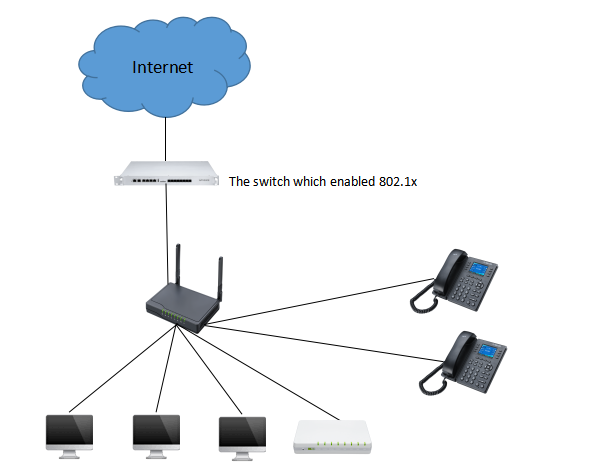
3. The Network Topological of TR-069
As shown in the figure, the company connects to the network through a switch with 802.1x authentication. All devices need to pass the switch to access the Internet. For convenience, you can use another bypass router to enable 802.1x client authentication. , and then all other types of terminal equipment are connected to the router's downlink. Or, you can also connect other audio equipments, such as telephones, directly under the switch, and also enable client authentication. The phone can also access the Internet normally.
4. Flying voice supported authentication methods
EAP-MD5
EAP-PEAP/EAP-MSCHAPv2
EAP-TTLS/EAP-MSCHAPv2
EAP-PEAP/GTC
EAP-TTLS/EAP-GTC










 volver a la lista
volver a la lista